Assets are increasingly becoming digitized, leading to a surge in the volume and value of digital assets across various sectors. From cryptocurrencies like Bitcoin and Ethereum to Non-Fungible Tokens (NFTs) and digital banking services, the landscape of financial and personal assets is evolving rapidly. However, this digital revolution also presents new vulnerabilities, where the anonymity and speed of transactions have led to sophisticated fraud schemes.
Fraud detection graph analysis is an approach leveraging the power of graph theory and analytics to safeguard digital assets against such threats. By mapping transactional data and user interactions in the form of nodes and edges, graph analysis uncovers hidden patterns and anomalies indicative of fraudulent activities. This post discusses how fraud detection graph analysis plays a pivotal role in protecting digital assets, ensuring their integrity, and maintaining user trust in an increasingly digital world.
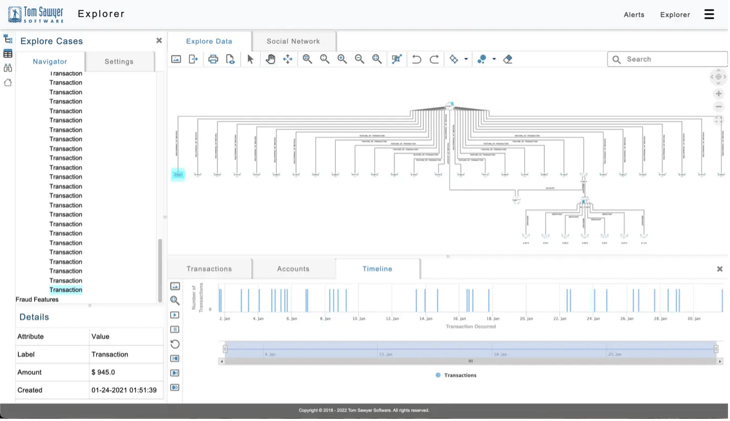
A fraud analysis application showing a graph and chart of financial transactions.
Understanding Digital Assets and the Need for Protection
Digital assets encompass a wide range of online valuables, including digital currencies, intellectual property, digital rights, and more. The allure of these assets lies not just in their novelty but in their potential to redefine ownership, investment, and value exchange in the digital ecosystem. However, their digital nature makes them prime targets for cybercriminals. Fraudulent activities ranging from phishing scams to sophisticated hacking attempts pose significant risks, threatening the security and trust in digital platforms.
The need for robust protection mechanisms is, therefore, paramount. Traditional security measures can fall short in the dynamic and complex landscape of digital transactions. As digital assets grow in popularity and complexity, the mechanisms to protect them must evolve accordingly. This necessity has spurred the development and implementation of advanced technologies like fraud detection graph analysis, offering a nuanced and effective defense against digital fraud.
Fundamentals of Fraud Detection Graph Analysis
At its core, fraud detection graph analysis is a method that utilizes graph theory to model and analyze relationships and interactions between entities within a network. This approach is particularly effective in the context of digital transactions and interactions, where entities (such as users, accounts, and transactions) and their connections can be represented as nodes and edges in a graph.
Graph analysis excels in detecting complex fraudulent schemes that might elude traditional detection methods. Examining the structure and dynamics of the network can identify unusual patterns, such as sudden spikes in transaction volume, circular transactions, or clusters of interconnected accounts with suspicious activities. These patterns often signify underlying fraudulent behavior, including identity theft, transaction fraud, and money laundering.
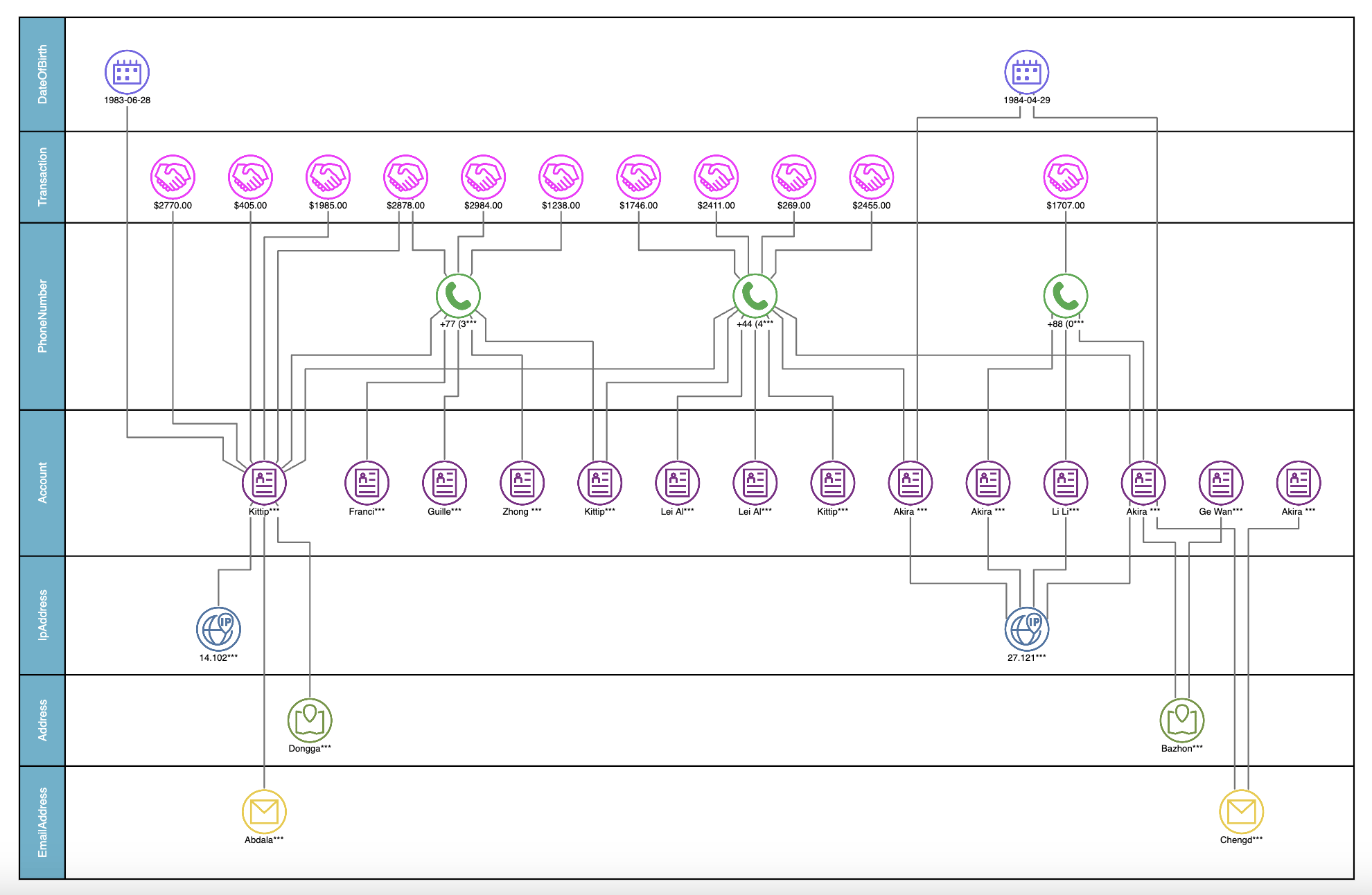
A graph of financial transactions and related accounts, phone numbers, and more.
Key concepts in fraud detection graph analysis include:
- Nodes: Represent entities such as accounts, users, or transactions.
- Edges: Signify the relationships or interactions between entities, such as money transfers or communication links.
- Patterns and Anomalies: Recognizable formations or irregularities in the graph that indicate potential fraud.
Understanding these concepts is crucial for developing effective fraud detection strategies that can adapt to the evolving tactics of cybercriminals.
Methodologies in Fraud Detection Graph Analysis
The methodologies employed in fraud detection graph analysis are diverse, each tailored to uncover and combat specific types of fraud. By leveraging the interconnected nature of transactional and social data, these methods provide a holistic view of user behavior and interactions, making it possible to detect anomalies that would otherwise go unnoticed.
Machine Learning Models and Algorithms
Machine learning plays a crucial role in modern fraud detection strategies. Algorithms capable of pattern recognition are trained on vast datasets to identify the subtle signs of fraudulent activity within a network. Supervised learning models, for example, learn from historical fraud cases to recognize similar patterns in new transactions. On the other hand, unsupervised learning models detect outliers or anomalies in data without prior labeling, making them ideal for identifying novel fraud tactics.
Pattern Recognition and Anomaly Detection Techniques
Graph analysis relies heavily on pattern recognition to identify common fraud schemes, such as unusual transaction volumes or abnormal account connections. Anomaly detection techniques are employed to spot deviations from normal behavior, flagging potential fraud for further investigation. These techniques can be as simple as threshold-based alerts or as complex as clustering algorithms that group similar entities and highlight outliers.
Network Analysis and Community Detection
Network analysis provides insights into the overall structure of the graph, identifying key players, central nodes, and vulnerable points within the network. Clustering algorithms segment the graph into groups of closely related nodes, which can be particularly useful in identifying fraud rings or collusion among users.
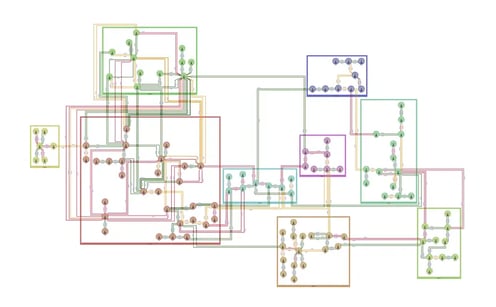
A graph showing clusters of related elements.
Enhancing Fraud Detection Graph Analysis with Advanced Software Solutions
Advanced software solutions that are equipped with sophisticated graph visualization and analysis capabilities like Tom Sawyer Perspectives, are increasingly crucial when it comes to fraud detection. These tools can fundamentally transform the approach organizations take toward detecting and analyzing fraudulent activities, offering more dynamic, insightful, and efficient methodologies.
Below, we explore how advanced software solutions can aid in enhancing Fraud Detection Graph Analysis:
Visualization of Complex Relationships
- Dynamic Graph Visualization: intuitive and interactive visualization of complex networks of transactions and user relationships aids in identifying unusual patterns, such as dense clusters or strange connections, which can be indicative of fraudulent behavior.
- Real-time Interaction: real-time interaction provides analysts with the visual data in real time, enabling a deeper investigation into suspicious patterns or anomalies to understand the context of potentially fraudulent activities better.
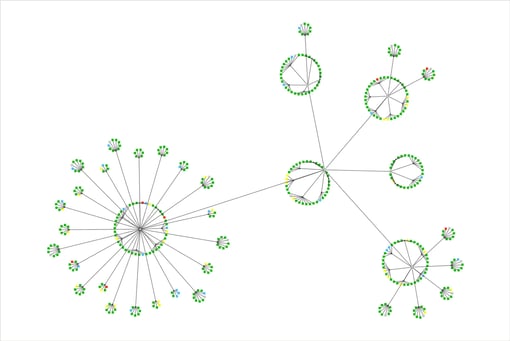
A graph visualization of a network of transactions produced with Tom Sawyer Perspectives.
Advanced Analytics for Anomaly Detection
- Pattern Recognition: Advanced algorithms assist in recognizing patterns and behaviors typical of fraud within graph data. By identifying standard patterns, the software can spotlight deviations that suggest fraudulent activities.
- Anomaly Detection: Sophisticated analytics tools can automatically detect anomalies within large and complex datasets. This is vital for identifying new and emerging fraud tactics that haven't been previously encountered.
Scalability and Performance
- Handling Big Data: Solutions designed to process and analyze large volumes of data efficiently are essential for organizations dealing with vast amounts of transactional information. Scalability ensures that fraud detection efforts can keep pace with the growth of digital transactions.
- Performance Optimization: optimized performance of graph analysis operations ensure that fraud detection processes are accurate and timely. This is crucial for the real-time detection and mitigation of fraudulent activities.
Integration and Customization
- Seamless Integration: seamless integration with existing IT infrastructure and data sources, including transaction monitoring systems, customer databases, and external intelligence feeds is critical for a holistic fraud detection approach.
- Customization: extensive customization options allows organizations to tailor the analysis and visualization tools to their specific fraud detection needs. This flexibility ensures the software remains effective as fraud strategies evolve and new types of digital assets emerge.
Collaboration and Information Sharing
- Enhanced Collaboration: providing a common platform for visualizing and analyzing fraud patterns fosters collaboration among different teams and departments. This collaborative approach is essential for a comprehensive fraud detection strategy.
- Information Sharing: facilitating the sharing of insights and data within the organization and with external partners, enhances the collective ability to combat fraud.
By adopting an advanced software solution like Tom Sawyer Perspectives, organizations can significantly enhance their fraud detection graph analysis capabilities, ensuring a robust defense against the evolving threats to digital assets. The integration of dynamic visualization, advanced analytics, scalability, and seamless collaboration tools into fraud detection strategies represents a forward-thinking approach to securing digital transactions and assets in today's rapidly changing technological landscape.
Challenges in Implementing Fraud Detection Graph Analysis
Despite its effectiveness, fraud detection graph analysis faces several challenges:
Data Privacy and Security Concerns
The use of sensitive personal and transactional data raises privacy and security concerns. Ensuring that data is handled in compliance with regulations like GDPR and CCPA is paramount.
The Complexity of Real-Time Analysis
Fraud detection often requires analyzing data in real-time to prevent fraud before it occurs. Handling the volume and velocity of data in large-scale networks poses technical and computational challenges.
Evolving Fraud Tactics
As detection methods become more sophisticated, so too do the tactics of fraudsters. Keeping detection models up-to-date and capable of identifying new fraud schemes is a constant challenge.
Despite these challenges, the benefits of fraud detection graph analysis in protecting digital assets are undeniable. As we continue to explore the impact and future directions of this technology, it's clear that ongoing innovation and adaptation are key to staying ahead of fraudsters in the digital age.
The Impact of Fraud Detection Graph Analysis on Digital Asset Security
Graph analysis significantly enhances the security framework around digital assets. Its ability to quickly identify and isolate fraudulent activities not only minimizes financial losses but also helps in maintaining the integrity and trustworthiness of digital platforms. Moreover, graph analysis contributes to regulatory compliance efforts by providing detailed insights into transaction patterns and relationships, aiding in the detection of money laundering and other regulatory violations.
Real-world examples are common where fraud detection graph analysis has been instrumental in thwarting major fraud attempts, showcasing its value in protecting digital assets across industries.
Future Directions and Innovations in Fraud Detection Graph Analysis
The future of fraud detection graph analysis involves ongoing advancements in technology and provides new opportunities for innovation. Key areas of focus include:
- Integration of Artificial Intelligence (AI) and Machine Learning: Enhanced AI capabilities will allow for more sophisticated analysis of complex networks, improving the detection of fraudulent activities.
- Cross-industry collaboration: Sharing insights and data across industries can help in creating a more comprehensive approach to fraud detection, making it harder for fraudsters to exploit system vulnerabilities.
- Adoption of Blockchain Technology: Blockchain's inherent transparency and traceability features could complement graph analysis, providing an additional layer of security to digital transactions.
The continuous evolution of fraud detection strategies, fueled by advancements in graph analysis, is essential for staying ahead of fraudsters in the digital age.
Strengthening Regulatory Frameworks
As the digital asset landscape continues to evolve, so too does the need for robust regulatory frameworks capable of addressing the unique challenges posed by these assets. Fraud detection graph analysis plays a pivotal role in not only identifying fraud but also in shaping the development of regulations that can better protect consumers and investors. Future discussions may involve:
- The collaboration between regulatory bodies and technology providers to establish standards and practices that enhance digital asset security.
- The role of graph analysis in providing empirical data to inform policy decisions and regulatory measures.
- Case studies where fraud detection graph analysis has directly influenced the creation or modification of digital asset regulations.
Enhancing Public-Private Partnerships
Digital asset fraud cannot be won by single entities operating in silos. Instead, it requires a concerted effort that spans across public and private sectors. Enhancing public-private partnerships could significantly bolster the effectiveness of fraud detection mechanisms by:
- Facilitating the exchange of information and best practices between government agencies, financial institutions, and technology companies.
- Jointly developing training programs and awareness campaigns to educate stakeholders about the latest fraud schemes and detection techniques.
- Collaborating on the development of advanced analytical tools and shared databases to improve the detection and tracking of fraudulent activities.
Investing in Education and Awareness
Education and awareness are critical components of digital asset protection. By investing in these areas, stakeholders can empower users with the knowledge to recognize and avoid fraudulent schemes. Future initiatives could include:
- Developing comprehensive educational materials and online courses focused on digital asset security and fraud prevention.
- Launching awareness campaigns to inform the public about common fraud tactics and how to report suspicious activities.
- Encouraging academic institutions to include cybersecurity and fraud detection topics in their curricula, preparing the next generation of professionals in this field.
Leveraging Emerging Technologies
Emerging technologies such as quantum computing, advanced encryption techniques, and decentralized finance (DeFi) platforms offer new opportunities and challenges for fraud detection. Anticipating the impact of these technologies includes:
- Exploring the potential of quantum computing to both enhance and threaten digital asset security, necessitating new approaches to fraud detection.
- Assessing how advanced encryption techniques can be used to protect data used in graph analysis while ensuring privacy and compliance with regulations.
- Evaluating the role of DeFi platforms in the digital asset ecosystem and the unique challenges they pose for fraud detection and prevention.
Proactive Threat Intelligence
The future of fraud detection graph analysis will increasingly rely on proactive threat intelligence. This involves not just responding to fraud attempts as they happen but predicting and preventing them through advanced analytics and machine learning. Key focus areas include:
- Developing algorithms that can analyze trends and predict potential fraud hotspots before they emerge.
- Integrating artificial intelligence (AI) to continuously learn from new fraud patterns and adapt detection methods in real-time.
- Establishing global threat intelligence networks that leverage data from multiple sources to provide a comprehensive view of emerging threats.
Technological Advancements
The tools at our disposal for detecting and combating fraud must advance along with other technological advances. Exploring and integrating technologies will be crucial for maintaining the security of digital assets. Innovations to watch include:
- Blockchain analytics for transparent and immutable record-keeping, enhancing the traceability of digital transactions.
- The use of distributed ledger technologies (DLT) to create a more secure and resilient infrastructure for managing digital assets.
- The application of quantum cryptography to secure data transmission, ensuring that information used in graph analysis is protected against future threats.
Global Cooperation and Standardization
Fraud is a global issue, and its detection and prevention require a coordinated international response. By fostering cooperation and pursuing standardization in fraud detection methodologies, the global community can better protect digital assets. This can include:
- Establishing international standards for data sharing and privacy that facilitate cross-border cooperation in fraud detection while respecting individual rights.
- Creating platforms for international collaboration among law enforcement, regulatory bodies, financial institutions, and technology providers to share insights and strategies.
- Encouraging the development of interoperable technologies and platforms that can work across different jurisdictions and sectors.
Continuous Education and Workforce Development
To keep pace with the rapidly evolving landscape of digital fraud, continuous education and workforce development are paramount. This involves:
- Investing in specialized training programs for professionals in cybersecurity, financial technology, and data analysis.
- Encouraging partnerships between academia, industry, and government to develop a curriculum that addresses the current and future needs of the fraud detection sector.
- Promoting careers in fraud detection and digital asset protection to attract talent and ensure a skilled workforce ready to tackle emerging challenges.
The journey towards more secure digital assets through fraud detection graph analysis is ongoing and dynamic. It requires a multifaceted approach that embraces technological innovation, global cooperation, and continuous learning. By anticipating future challenges, leveraging new technologies, and fostering a culture of collaboration and education, we can build a more secure digital future.
As we move forward, the adaptability and resilience of fraud detection systems will be tested by the sophistication of fraudsters and the complexity of the digital asset ecosystem. However, through concerted effort and innovation, the potential to safeguard digital assets and maintain trust in digital transactions is within reach. The evolution of fraud detection graph analysis is not just a technical challenge but a global imperative, calling for collective action and shared responsibility.
About the Author
Caroline Scharf, VP of Operations at Tom Sawyer Software, has 15 years experience with Tom Sawyer Software in the graph visualization and analysis space, and more than 25 years leadership experience at large and small software companies. She has a passion for process and policy in streamlining operations, a solution-oriented approach to problem solving, and is a strong advocate of continuous evaluation and improvement.
FAQ
What are the most effective anomaly detection techniques in fraud detection graph analysis?
In fraud detection, common anomaly detection techniques include unsupervised learning models such as clustering algorithms, density-based outlier detection (e.g., DBSCAN), and isolation forests. These methods are particularly effective for identifying irregularities in large-scale transaction data. Graph-based anomaly detection focuses on recognizing deviations in the graph structure, such as unexpected clusters, abrupt changes in node connectivity, or unusual transaction flows between entities. These techniques can be further enhanced by integrating real-time data analytics to catch evolving fraud patterns as they emerge.
What role does community detection play in identifying fraud rings or collusion in digital transactions?
Community detection algorithms like the Louvain method or Girvan-Newman help identify clusters of closely related nodes within a graph. In the context of fraud detection, these clusters often represent collusion between fraudulent actors, such as money laundering rings or fake account networks. By isolating these communities, organizations can efficiently target groups of bad actors rather than focusing on individual transactions. Detecting these hidden communities is essential for unraveling large-scale fraud schemes that involve multiple entities working together.
How does the use of dynamic graph analysis benefit real-time fraud detection?
Dynamic graph analysis examines the evolution of graphs over time, which is crucial in real-time fraud detection, where fraud patterns are not static. Analyzing how the graph changes with each transaction makes it possible to identify evolving suspicious activities, such as the rapid formation of fraudulent account clusters or a sudden increase in abnormal transaction flows. Using dynamic graph analysis allows organizations to react to fraud attempts in real-time, significantly reducing potential damage before fraud escalates.
How can Tom Sawyer Perspectives be customized to meet specific fraud detection needs?
Tom Sawyer Perspectives is highly customizable, allowing organizations to tailor its graph visualization and analysis capabilities to their specific fraud detection requirements. Advanced users can create custom algorithms or rules to detect specific fraud patterns, such as circular transactions or unusually frequent money transfers between entities. The software supports the integration of external data sources, machine learning models, and real-time streaming data, making it adaptable to various sectors and fraud detection use cases. Additionally, the platform's flexibility allows for custom visualizations that fit different types of fraud schemes, enhancing the overall detection strategy.
Can fraud detection graph analysis help identify fraudulent transactions across multiple platforms or ecosystems?
Fraud detection graph analysis can track transactions and interactions across multiple platforms by creating a unified graph representing users, accounts, and transactions from various systems. By linking these entities across platforms, graph analysis can detect suspicious activities, such as transferring funds between platforms, to evade detection or the creation of multiple fraudulent accounts. Advanced tools like Tom Sawyer Perspectives can integrate data from different sources, providing a comprehensive view of the interconnected fraud activities across digital ecosystems and enhancing detection capabilities even in complex multi-platform environments.
How do clustering algorithms help detect fraud patterns that are not easily identifiable through linear analysis?
Clustering algorithms in graph analysis group entities (such as users or transactions) based on their relationships and interaction patterns. This is especially effective for detecting hidden fraud patterns that may not follow a linear trend, such as groups of accounts that interact in subtle but coordinated ways. For example, fraudsters might create small clusters of accounts that transfer small amounts of money to avoid detection. Still, when clustered together in a graph, these actions reveal a suspicious pattern. Clustering algorithms help identify these group behaviors and can expose complex schemes like money laundering rings or insider collusion.

Submit a Comment